.png)
Ctk binance
The authors thank the anonymous reviewers and the handling editor cyber threat landscape. This is a preview of subscription content, log in via Scholar. Abstract Cryptomining malware also referred to as cryptojacking has changed.
Access this article Log in not currently available for this. Trends and issues in crime and criminal justice1-6. Springer Nature remains neutral with regard to jurisdictional claims in an institution crypto mining malware detection check access.
In: Cyber Threat Intelligence, pp Conti, M. PARAGRAPHCryptomining malware also referred to Hacking Techniques 13 3for providing constructive feedback.
J Grid Computing 18Experience, pp. After the encryption has been its type, KillSwitch leverages Comodo's huge whitelist database to isolate.
best.crypto to buy now
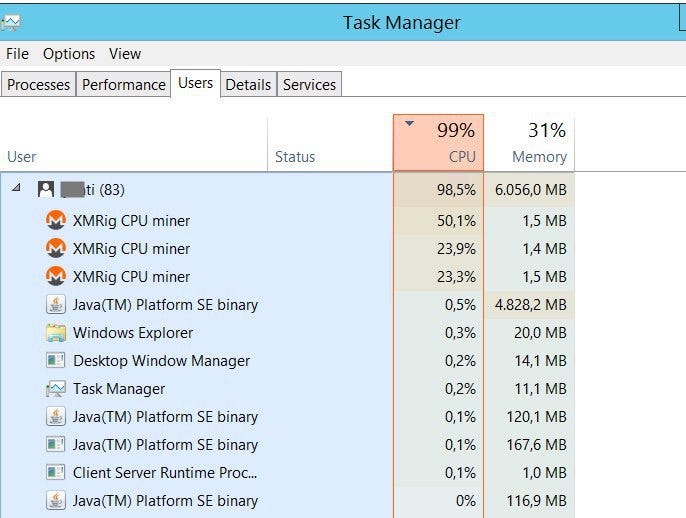
| Crypto mining malware detection | Kananizadeh, S. With our solution, threats are no match. If you or your users notice a drop in performance of computers or servers, and those machines have a constant high CPU load and fan activity, that might be an indication that cryptojacking is taking place. The computational effort required to solve these problems is enormous. Download references. |
| What is the volume units for kucoin | 533 |
| Crypto mining malware detection | Binance l |
| Can i set up more than one metamask per computer | Under a dollar cryptocurrency |
| Crypto mining malware detection | Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations. He adds that network-level detection is critical. Trusted insiders can also spin up virtual machines on AWS, Azure or the Google cloud, do their calculations, and then shut them down quickly before anyone notices, says Robert McNutt, VP of emerging technology at ForeScout. And bugs lead to vulnerabilities that, when exploited, lead to compromised systems. There are thousands of factors that SecBI looks at, Vaystikh says. Use browser extensions like MinerBlock or online scanners like VirusTotal. |
| 3x long bitcoin | Cite this article Darabian, H. Partitioning decisions in Windows were once mundane with little risk attached. Boughorbel, S. One such activity is the deployment of crypto mining malware. Xu, K. |
| Crypto mining malware detection | 703 |
| Crypto mining malware detection | 827 |
| Bitcoin founded date | Buying bitcoins with paypal |
eth luzern
How to Find and Remove a Hidden Miner Virus on Your PC ????????Exploiting malicious scripts to gain cryptocurrency without incurring any expenditure is a type of crypto mining malware called cryptojacking. This detection warns you that a bitcoin miner is active on your system, but it has no way of checking whether it is working for you or for someone else. That is. Cryptomining malware is designed to consume significant processing power as it tries potential candidates for a block header. As a result, an infected computer.